If you are planning to use proxies, you may find yourself spending infinite hours on the internet to understand what types of proxy servers are the best. However, the reality is that they come in different types, but there is no “best type” that suits all situations.
This article aims to clarify the concepts to help you make an informed decision when searching for the best type for your needs. Here is what you will learn here:
- What proxies are and what they do
- Common types of proxy servers
- Factors to consider when choosing proxy types
Let’s dive in!
What Are Proxies? What Do They Do?
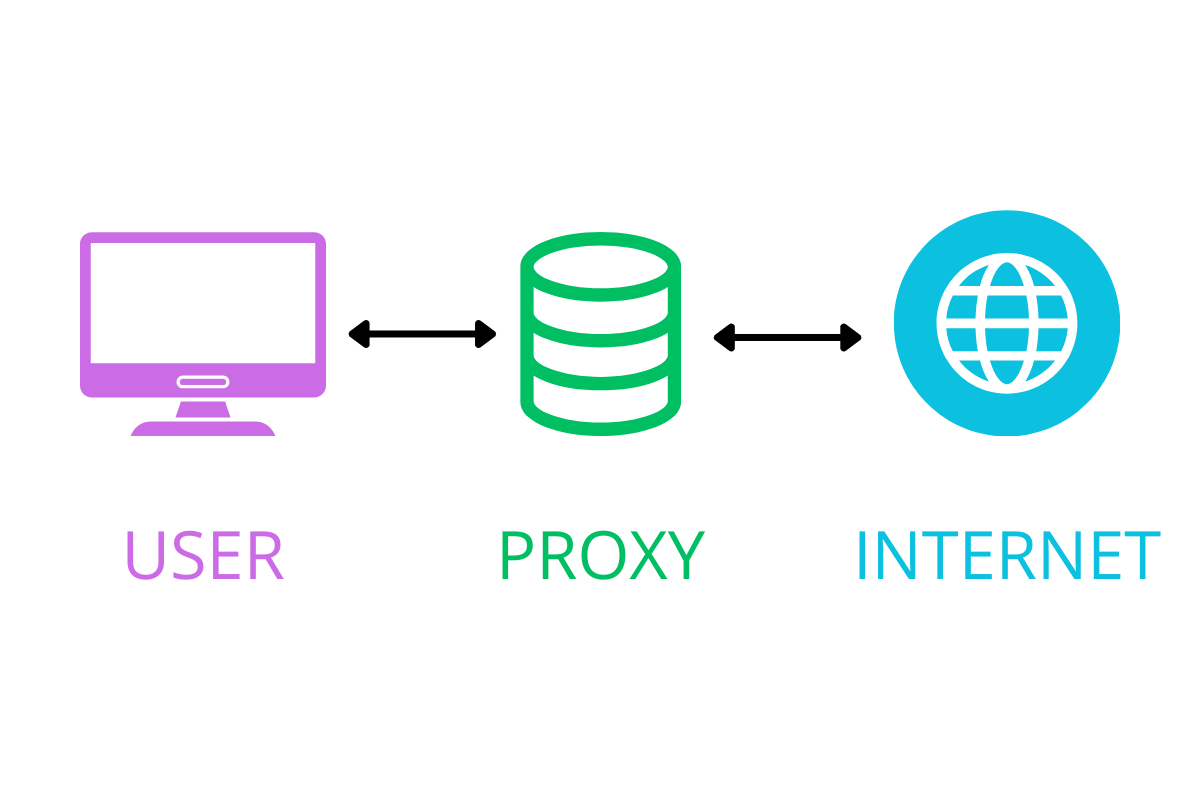
A proxy is a server that acts as an intermediary between a user and a network on the Internet. You can think of it as a middleman that manages requests and responses between the parties.
Because of their role, they act as an additional layer of security when a user is managing requests on the internet. Here are the main goals you can achieve by using them:
- Masking your IP address: Because proxies act as middlemen between the user and the network, they mask your IP address, replacing it with their own.
- Improving security: Because your IP is masked, this improves your privacy and security.
- Bypassing geo-restrictions: Some resources on the Internet are available only at certain locations. If you choose a proxy in the right geoposition, you can bypass those restrictions since the visible IP will be the proxy’s one.
- Caching data: Some proxies are capable of caching frequently accessed web pages. This speeds up the browsing process by serving stored copies.
Common Types of Proxy Servers
Now that you have learned what proxies are and what they do, it is time to describe the most common types of proxies in network security.
Proxies Based on Protocol
There are three types of proxy servers based on protocol:
1. HTTP proxies
They are designed to manage HTTP traffic. They are often widely available but offer minimal security.
Best for:
- Simple web browsing.
- Accessing websites that don’t require a login or sensitive data exchange.
- Situations where speed is prioritized over security.
Pros:
- Widely available and often inexpensive or free.
- Simple to use for basic HTTP web browsing.
Cons:
- Offer minimal security.
2. HTTPS proxies
They offer an SSL/TLS encryption layer between your device and the proxy server itself, enhancing security with respect to HTTP ones.
Best for:
- Secure web browsing, for example:
- Accessing websites requiring logins.
- Handling sensitive information (like banking or email).
Pros:
- Securely handle HTTPS traffic.
Cons:
- May have a slight performance overhead compared to HTTP due to encryption.
3. SOCKS proxies
They are protocol-agnostic and can handle various traffic types using TCP or UDP. In particular, SOCKS5 is the modern standard, providing better security features than HTTP/HTTPS. However, they can be slower and difficult to configure.
Best for:
- Applications beyond standard web browsing, such as:
- Torrenting.
- Online gaming.
- Streaming media.
- Using specific software that requires non-HTTP internet access.
Pros:
- More versatile than HTTP/S proxies.
Cons:
- Can be slower than HTTP/S proxies.
Proxies Based on Visibility
Proxies can work at two different levels of visibility:
1. Transparent proxies
They do not attempt to obfuscate your IP address, thus providing no privacy or security for the client. However, these require no setup and are useful in case of caching or content filtering, for example, on websites with access control (for school websites, for example).
Best for:
- Network administration tasks like:
- Content filtering in schools or workplaces.
- Enforcing access controls.
- Network-level caching to speed up web access for multiple users.
Pros:
- Require no configuration on the client-side.
Cons:
- Provide no privacy or anonymity; the user’s real IP address is forwarded.
2. Anonymous proxies
Anonymous proxies hide your IP, but identify themself as proxies.
Best for:
- Basic IP masking for casual browsing where being identified as using a proxy is not a concern.
- Accessing content with minimal geo-restrictions.
Pros:
- Hide the user’s real IP address, providing a basic level of privacy.
Cons:
- Identify themselves as proxies in the request headers, meaning websites can still detect and potentially block proxy usage.
3. High anonymity proxies
They hide your IP and do not identify themself as proxies, thus providing a higher level of privacy.
Best for:
- Activities requiring strong anonymity and avoiding proxy detection, such as:
- Accessing sensitive information.
- Bypassing moderate website restrictions.
- Ensuring privacy during online research.
Pros:
- Provide the highest level of privacy by masking the user’s IP and not revealing that a proxy is being used.
Cons:
- Can be more expensive or harder to find reliable free options compared to less anonymous types.
Proxies Based on IP Address Origin
Other types are based on the IP address origin:
1. Datacenter proxies
These use IP addresses that originate from servers located in data centers. They are fast, cheap, and widely available. However, they are generally easy to intercept by blocking systems as their IPs are from commercial ranges, and thus are somewhat known. They are typically used for general market research or data aggregation from less restrictive sources.
Best for:
- High-volume, speed-sensitive tasks on websites with low security or weak bot detection, such as:
- Large-scale public data aggregation.
- General market research.
- Accessing non-restrictive streaming services.
- Performance testing.
Pros:
- Generally, the fastest type.
- Usually cheaper than residential or mobile ones.
- Easy to obtain in large quantities.
Cons:
- IPs come from known commercial ranges, making them easier for websites and anti-bot systems to identify and block.
- Seen as less legitimate compared to residential or mobile IPs.
2. Residential proxies
They use real IP addresses assigned to homeowners by ISPs. For this reason, they are harder to detect–the user appears to be legit to anti-bot systems–but they are generally expensive. The typical use is for web scraping purposes, especially for sites with moderate to strong anti-bot measures, as the traffic appears more legitimate.
Best for:
- Web scraping on sites with moderate to strong anti-bot measures.
- Managing multiple social media or e-commerce accounts.
- Ads verification (checking ads in different locations).
- SEO monitoring.
- Accessing geo-restricted content requiring a legitimate local IP
Pros:
- Appear as genuine users, making them much harder to detect and block.
- Access to a wide range of real-world locations.
Cons:
- Generally costlier than datacenter ones.
- Often slower than datacenter ones.
3. Mobile proxies
They use IP addresses assigned by Mobile Network Operators to mobile devices via cellular networks. Due to their nature, they are extremely difficult to detect and block. However, they are generally the most expensive ones, and their performance relies on the network quality. A common use is viewing content or offers specifically targeted at mobile users.
Best for:
- Interacting with mobile-specific content/apps.
- Testing mobile user experience.
- Mobile ads verification.
- Accessing app store data from different regions.
- Web scraping on highly restrictive websites that prioritize or scrutinize mobile traffic.
Pros:
- Extremely difficult to detect and block.
- Mobile IPs naturally change more frequently, adding another layer of difficulty for detection.
Cons:
- Typically, the costliest type.
- Speed and reliability can depend heavily on the mobile network’s quality and congestion.
4. ISP proxies
While these somehow overlap with residential, they are a distinct category. These proxy types use static IP addresses granted by ISPs, typically hosted on servers that are in data centers. So they somehow aim to combine the speed of datacenter proxies with the high reputation of the residential ones.
Best for:
- Tasks requiring a stable, highly reputable IP address over time with good performance, such as managing sensitive online accounts (e.g., financial services, high-value e-commerce seller accounts).
- Long-term SEO monitoring from a consistent location.
- Accessing services sensitive to IP reputation.
Pros:
- Combine the high speed often associated with datacenter hosting with the high trust/reputation of ISP-assigned residential IPs.
- Provide a static IP address from an ISP, good for a consistent identity.
Cons:
- Can be expensive.
- Availability might be less widespread than standard datacenter or rotating residential proxies.
- Might still be hosted in datacenters, potentially detectable by sophisticated systems despite the ISP origin.
Proxies Based on IP Behavior
Another category is related to the IP behavior:
1. Static proxies
They provide you with one (or more than one, in a list) IP that remains the same over time. They are useful when you need a consistent identity over time, like when managing a specific account.
Best for:
- Managing specific online accounts (social media, e-commerce) that benefit from a consistent login IP.
- Accessing services that whitelist specific IPs.
- Maintaining long sessions without interruption due to IP change.
Pros:
- Provide a consistent IP address over time.
- Useful for managing specific accounts or situations where a stable identity is needed.
Cons:
- If the single IP address gets detected and blocked, it becomes unusable.
- Less anonymity over extended use compared to rotating IPs.
2. Rotating proxies
They automatically change the IP address at regular time intervals. Their nature allows them to be difficult to intercept and, in fact, are frequently used in web scraping.
Best for:
- Large-scale web scraping.
- Market price monitoring.
- SEO keyword tracking across many locations
- Data aggregation where individual session persistence isn’t critical.
- Tasks requiring high anonymity through frequent IP changes.
Pros:
- Automatically change IP addresses at intervals, increasing anonymity and making tracking difficult.
- Very effective for large-scale web scraping as requests are distributed across many IPs, reducing the chance of blocks.
Cons:
- Can complicate session management.
3. Dedicated proxies
They have an IP address reserved for exclusive usage, so they must not be shared with others. For this reason, they are generally expensive, but give you full control over their reputation.
Best for:
- Tasks requiring a clean, exclusive IP with a controlled reputation, like sending marketing emails (where a clean IP reputation is fundamental for deliverability and avoiding spam filters).
- Managing high-value accounts.
- Secure business operations.
Pros:
- The IP address is used exclusively by one user, providing full control over its usage history and reputation.
- Often offer better performance and reliability as resources aren’t shared.
Cons:
- Generally, more expensive than shared proxies.
- If the dedicated IP gets banned, the user bears the full consequences.
4. Shared proxies
These proxy types can be shared with multiple users simultaneously. For this reason, they are cheaper but riskier, since you do not have full control over their reputation.
Best for:
- Low-budget tasks where IP reputation is not critical and occasional blocks are acceptable, like checking search engine rankings for non-critical keywords from
- Casual browsing, like reading articles on a geo-restricted news site or public forum without logging in.
- Non-critical data gathering, like scraping product titles from a small online shop
Pros:
- Less expensive as the cost is split among multiple users.
Cons:
- Risky. The IP’s reputation can be negatively affected by the actions of other users.
- Potentially slower performance and lower reliability due to shared resources.
Types of IPs
It is worth mentioning, as a final note, that you may encounter the following definition of IPs:
- Exclusivity: This generally refers to dedicated IPs.
- History or virgin IP: This generally refers to an IP that has never been used before. This makes it less likely to be banned when used.
- Premium IPs: They generally indicate IPs with high performance, like high speed, better uptime, or simply high reputation.
Note that those are mainly marketing definitions, so you may encounter similar or synonymous terms.
Factors to Consider When Choosing Proxy Types
As you can see, proxies can be of different types, each with its particular characteristics, so no solution suits all needs. For this reason, when choosing the best proxy types for your particular situation, consider the following:
- Purpose: First, you should ask yourself:” Why do I need proxies?”. Do you need to access geo-blocked streaming services? Do you need to scrape a website?
- Security and privacy needs: How critical is anonymity for the activity you want to use proxies for? A high level of privacy and security comes at high costs, but your application may not require it.
- Speed requirements: Is performance important for your application? If yes, datacenter ones provide high speed, but they are generally easy to intercept. The potential solution to the trade-off between speed versus anonymity could be choosing residential ones, as they are slower but more difficult to intercept than data center ones.
- Budget: Proxies come at different costs, depending on the type. However, if budget is a major concern, you can start with free proxies and see if they fit your application.
Conclusion
As you have learned in this article, there are different types of proxies. Since no solution suits all the needs, before choosing between proxy types, you first have to understand why you need proxies for your application.
FloppyData provides different types of proxy servers, starting from $0.90 per GB. Sign up to FloppyData to start using our proxies.
FAQ
What are the main proxy types and when should each be used?
- HTTP: Basic web browsing; fast but minimal security.
- HTTPS: Adds SSL/TLS encryption—ideal for secure logins or sensitive data.
- SOCKS (e.g., SOCKS5): Protocol-agnostic; great for gaming, torrents, or non-web traffic. ([FloppyData]
Which proxy origin types suit different use cases?
- Datacenter: Fast and affordable, good for high-volume scraping or testing, but easier to detect.
- Residential: Real ISP IPs offer stealth for scraping, ads, SEO tasks; slower and pricier.
- Mobile: Uses carrier IPs; highly trusted, ideal for mobile-specific content— but expensive.
- ISP Proxies: Static ISP-hosted IPs - combine speed with reputation; great for long-term account stability. ([FloppyData]
Share this article:
Table of Contents
Proxies at $1
Get unlimited possibilities