Internet users have become more concerned about their online privacy as our collective reliance on the web increases. They wish to avoid targeted ads, identity theft, personal data leaks, and obstructions to their browsing experience. So, they use an anonymous proxy service to maintain their anonymity online. A high anonymous proxy masks the user’s IPP address. It acts as a bridge between the user’s device and the destination server. So, you can anonymously visit different websites using an anonymous proxy.
However, some Internet users are still doubtful about the safety and effectiveness of these proxies. Are they completely risk-free with no downgrades at all? Do anonymous proxy services successfully conceal your search history from websites collecting cookies? It’s true that not all proxies provide the same level of protection; some low-quality proxies may even compromise user data in lieu of safeguarding it. What is even more concerning is that a lot of websites easily detect (and even bypass) the usage of proxies.
So, how do you circumvent the “proxy detected” error? A website may block you from seeing its content if you’re using a normal proxy. It’ll create something like a cat-and-mouse game between users sending requests to the target server seeking anonymity and organizations blocking your request, assuming that it is coming from a shady source. The potential for data leakage, man-in-the-middle attacks, or exposure to malware adds another layer of complexity here. So, you should carefully navigate these risks.
This blog will explain how to use an anonymous proxy server without detection. That’s how an Internet user can maintain their privacy & anonymity while warding off the dangers associated with using proxies generally. We’ll also explain how to deal with the “anonymous proxy detected” error successfully.
What does Anonymous Proxy Detected Mean?
Have you ever tried using a proxy and were hit with the “proxy detected” error message? It means that the target website knows that you’re trying to access its content by using an anonymous proxy. In other words, your access request gets flagged by that website.
It happens because websites want to prevent access of unauthorized access or abuse (especially when they think that a fair chunk of the Internet traffic is made of bots!). So, the site’s security protocols stop you from accessing the website or its content.
A site may flag your connection as originating from anonymous proxies and restrict your access, thinking that it might lead to fraud or abuse. That’s because many scammers utilize their proxies to bypass a lot of geographical restrictions and engage in malicious activities (like posing as someone else to scam genuine consumers). That’s how you often get the “anonymous proxy detected” on your screen.
In simple words, this message serves as a warning that a site has successfully identified your connection as potentially suspicious. That’s why you should use an anonymous proxy service very carefully.
How Do Anonymous Proxies Work?
Did you know that every 4th Internet user in the world right now is using anonymous proxies or a virtual private network (VPN)? Anonymous proxies also go by the term anonymizers. They hide a web user’s IP (and other identifying traits) by acting like a bridge between the user’s phone and the target site.
You can enhance your browsing experience by routing web traffic through these proxies. We’ll look into how proxies work in this section. But first, let’s discuss the historical evolution of anonymizers.
The Historic Evolution of an Anonymous Proxy Server
Proxy servers helped with caching web content to hone loading speeds in the early days of the Internet. But their role improved significantly as concerns regarding data privacy grew over time. Then, the rise of online surveillance and targeted ads made Internet users more concerned about data privacy. This led to the creation of anonymous proxies designed especially to mask IP addresses.
The Working of Anonymous Proxy Services
An anonymous proxy works like this:
- User Request: The user sends a request to access a website.
- Request Interception: The proxy will intercept this request so it doesn’t go straight to the target site.
- IP Masking: The proxy hides the user’s IP and sends its own IP. It then forwards the request to the destination server.
- Request Forwarding: The target website receives the modified request.
- Response Handling: The destination server processes these requests, sending the requested data back to the proxy server.
- Data Relay: The user’s device gets the website’s data from the proxy and the user sees the web content on their phone screen.
Levels of Anonymous Proxies
Experts categorize anonymizers into three major types. The level of IP address masking users get depends on the type of proxy you’re using.
-
Elite Proxies
These high anonymous proxies provide the best IP address masking possible. Using an elite proxy masks the user’s IP address completely to make sure that the destination server can’t detect proxy usage at all. Elite proxies do that by stripping away all identifying headers from the requests sent to the target sites.
- No Exposure: The target website gets absolutely no info about the user’s real IP address.
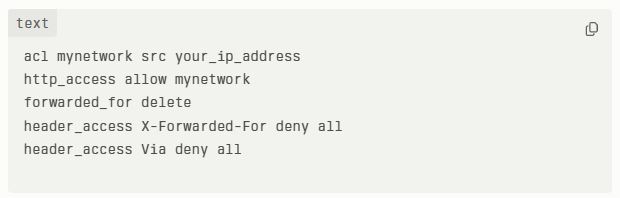
- Header Removal: The proxy makes it almost impossible for websites to detect the proxy usage by removing headers like “Authorization,” “X-Forwarded-For,” “Via,” “Proxy-Connection,” and “From.”
- Ideal Usage: This option is perfect (though expensive) for big-time users, such as journalists and whistleblowers. They can access sensitive info on governments without giving away their actual identities.
-
Anonymous Proxies
These midrange distorting proxies offer moderate levels of anonymity. They do hide a user’s IP address from the target server but not the fact that a proxy is being used.
- IP Masking: The target website doesn’t know the user’s real IP address, but this proxy may fail to hide all identifying information and the user’s data successfully.
- Partial Disclosure: This proxy may not conceal certain headers like “Via” when sending requests with a masked IP.
- Ideal Usage: This option is suitable for users who don’t need the utmost security. So, users who are interested in casual browsing only can use this option, or someone who wants to access content restricted in their homeland.
-
Transparent Proxies
These proxies provide the least levels of anonymity imaginable. They don’t hide the user’s IP address or the fact that a proxy is in use. They simply perform functions like caching or content filtering.
- No Anonymity: The target website can still see the user’s IP address and even trace the user’s online activities (possibly not their search history).
- Header Inclusion: The requests sent by these proxies typically include the user’s real IP address as well as the proxy’s address in visible headers that say “X-Forwarded-For.”
- Ideal Usage: Users don’t use such proxies to anonymize their browsing experience. Instead, they may utilize them in organizational settings where they desire to monitor Internet usage.
Why Should You Use an Anonymous Proxy?
Internet users install anonymous proxy services for various reasons. Some reasons include:
- Ascertaining Online Privacy: Hiding & masking your IP address prevents websites or advertisers from tracking your online activities. Some powerful proxies even stop your ISP from monitoring your browsing history.
- Access Restricted Content: You can easily access geo-restricted content by using a proxy server. These anonymous proxies bypass government restrictions so users can access content blocked in their countries. For instance, countries where X (formerly Twitter) or TikTok are blocked.
- Avoiding Cybersecurity Threats: Proxies may even deter cybersecurity threats for Internet users by coming in between their devices and potential viruses. So, proxies protect the user’s data and personal info from hackers by concealing their IP addresses.
- Evading Targeted Ads: Users can also avoid seeing targeted ads by using proxies. That’s because marketers track a user’s online browsing behaviors to send them personalized ads. But proxies obscure the user’s search history and don’t let marketers know which websites the user visits.
- Preventing Identity Theft: Masking the user’s IP address reduces the chances of identity theft, too. Cybercriminals don’t get access to your personal data and your real IP address stays hidden.
- Accelerating Internet Speeds: As we’ve explained before, early Internet users used anonymous proxies to cache frequently visited websites. They made these sites load faster the next time the user visited them by retrieving cached data instead of fetching it all from scratch.
Setting Up Anonymous Proxies
Setting up an anonymous proxy is possible whether you use a dedicated server or configure it on your local device. This section will focus on setting up a virtual private server (VPS) with software like Squid.
Choose Your VPS
You should choose a credible VPS provider like Linode or DigitalOcean. After you’re done selecting a VPS provider, create a new VPS instance with a Linux distribution mechanism (Ubuntu, for instance). You can access your server via SSH by typing this command:
Update Your Server
The next step is to make sure that your server is up-to-date and running.
Install a Proxy Server
You will now install the popular proxy server app Squid.
Please verify your installation.
Configure Squid
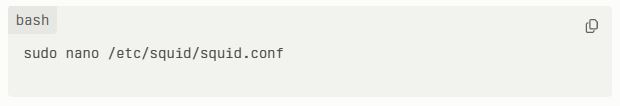
When you’re done with the previous step, you should open the configuration file.
Don’t forget to modify settings to make it better at masking your IP address.
Also, set the desired proxy port (default is 3128).
Restart Squid
Now, you’ll restart the Squid service to apply the changes.
Configure Firewall
Keep in mind that traffic on the proxy port should be allowed if you’re using a UFW (Uncomplicated Firewall).
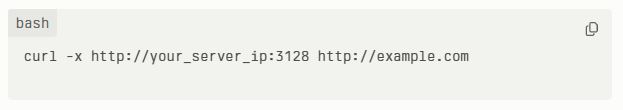
Test Your Proxy Figure
You will then enter the IP address and port of your server so you can configure your web browser to use the proxy. Another method is to test the proxy via a cURL command line.
Secure Your Proxy Server
This last step isn’t mandatory but only optional. You’ll have to enable authentication by modifying your Squid configuration. That’s how you’ll include authentication mechanisms to restrict access.
Resolving the “Anonymous Proxy Detected, Click Here” Error
If you’re getting the “anonymous proxy detected” message, you can resolve this error by following these simple steps:
- Terminating All Apps: You should close all open applications that may be using the proxy.
- Clearing Cache Data: The next step is to remove all cache data and cookies from your browser. This data may be signaling to the destination server that you’re masking your real IP. So, removing the cache will reset your session.
- Requesting a New IP: Many proxy providers support IP rotation. So, you can request a new IP to avoid detection.
- Using a High-Quality Proxy: Why don’t you switch to a more reliable proxy server? Low-quality servers fail to bypass sophisticated detection measures.
- Choosing a VPN: You can also mask your identity by using a virtual private network (VPN). A VPN encrypts your personal information, too.
Bottom Line
We learned that anonymous proxies hide a user’s browsing activity by masking their real IP address. But some websites use sophisticated measures to detect which users are using a proxy server. You can avoid that by deleting your cache data or simply requesting a new IP address from your host. That’s how you can evade detection and browse the Internet without getting flagged for proxy usage.
FAQs
What does the "Anonymous Proxy Detected" message mean?
The “Anonymous Proxy Detected” error appears when a website recognizes your connection as coming through an anonymizing proxy—often due to flagged IPs or visible proxy headers. This triggers security blocks, as sites treat these connections as potential bots or fraud.
How can I use proxies without being detected?
Use high-quality, rotating residential proxies to stay under detection thresholds. Rotate IPs regularly, clear cookies, and avoid sending identifying headers. Pair with an anti‑detect browser (like Multilogin or Gologin) to mask fingerprints. Paid services like FloppyData provide cleaner IPs and better anonymity.
Share this article:
Table of Contents
Proxies at $1
Get unlimited possibilities