Proxies are important in ensuring visibility control and online security in this generation. Two types of proxies that stand out in importance to businesses and individuals are the HTTP proxy and the HTTPS proxy. The target functions of these proxies are related as they are both positioned between the client and the internet – the point of distinction, nonetheless, is that while they are both essential for web usage, only one offers security through encryption.
Knowing such differences is necessary in order to opt for the right proxy in relation to a variety of activities, such as anonymous browsing, unblocking certain areas of content, and transferring sensitive data.
In this article, we will review the operational specifics of HTTP and HTTPS proxies, their similarities, as well as what sets them apart, and their distinct use cases. Based on their scope of applicability and effectiveness, we intend to elucidate how these proxies work and which one to use in a given scenario. For anyone who engages with the internet, be it an ordinary user or a professionally trained IT expert, comprehending how the two proxies function is a good starting point for enabling more practical and secure activities online.
What HTTP and HTTPS Have in Common and What Is Different
HTTP and HTTPS proxies are based on the same grounds, except their difference is in how data security and encryption are handled. We’ll break down their similarities and differences:
What HTTP and HTTPS Proxies Have in Common
| Feature | Description |
|---|---|
| Proxy Purpose | Both act as signals translating users’ requests and clients’ responses. |
| Traffic Routing | Both utilize a proxy server to assist in managing user requests and server responses. |
| IP Masking | Both assist users in maintaining anonymity by obscuring the original IP address. |
| Content Filtering | Both enable and disable website access based on specific requirements. |
| Performance Optimization | Both assist users in improving the efficiency of a network by reducing the burden on the server and storing particular data. |
Both proxies are intermediaries in the exchange of data between clients and servers. They have a similar communication role in relation to mass management, combatting malicious content, enhancing the speeds of the network, and masking IP addresses. The main objective is controlled access, and management of the web data.
What Is Different Between HTTP and HTTPS Proxies
| Feature | HTTP Proxy | HTTPS Proxy |
|---|---|---|
| Data Encryption | Does not encrypt data; information is sent in plain text. | Encrypts all data using SSL/TLS protocols. |
| Security Level | Vulnerable to eavesdropping and data interception. | Secure against interception and eavesdropping. |
| Use Case | Suitable for non-sensitive data and caching static content. | Ideal for handling sensitive information like login credentials and payment details. |
| Speed | Generally faster due to lack of encryption overhead. | Slightly slower because of encryption processes. |
| Port Used | Commonly uses port 80. | Commonly uses port 443. |
Proxies for HTTPS are more inclined towards security and privacy through SSL or TLS encryption and are thus perfect for transactions of a sensitive nature; however, they do not have the required efficiency as they focus on speed. The opposite is the case for proxies that utilize the HTTPS framework, as they tend to offer more speed but are highly inefficient in staying blunt on security communication as they lack encryption.
Understanding HTTP
The hypertext transfer protocol (HTTP) enables the transfer of hypertext over the internet. HTTP serves as a communication protocol between users, web pages, files, servers, and even webpages, enabling people to perform operations efficiently. An HTTP proxy enables communication by specifying a request on behalf of a client to a server and relays the relay of a don’t reply to the client. These are frequently implemented for static content, which decreases load times and manages bandwidth use.
During an HTTP request, data is sent in unencrypted form, leading to the fundamental flaw in HTTP – lack of security. The sheer light in which the data is passed today makes it prone to tapping and snooping, not to speak of the slew of boasts in which it could be breached. Although its use would be the result of major security bottlenecks, these users have become used HTTP proxies for security unfocused tasks like content filtering, web-based data extraction, or even website scraping, geo-location restriction access, etc.
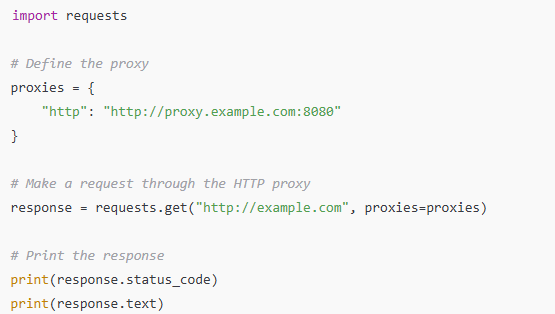
Example of an HTTP Proxy Configuration
For illustration, below is a code snippet that establishes an HTTP proxy through the requests authentication library in a Python script:
Explanation
- The proxies dictionary outlines the HTTP proxy address.
- Using the proxy, requests.get issues a GET request to the specified URL
- The response is shown with the webpage code and its content.
This shows how an HTTP proxy can be set up and utilized with Python for web requests.
Understanding HTTPS
The Hypertext Transfer Protocol Secure(HTTPS) is the standard for all web pages and transactions on the Internet. It has the potential of being even more secure than its predecessor HTTPS. Using an SSL/TLS (Secure Sockets Layer/Transport Layer Security) allows protection of the transferred data, which is essential for online transactions. It is widely accepted that tools such as HTTPS proxies are the best option for sensitive information as they possess optimal data encryption.
Just like the HTTP proxies work, the HTTPS proxies also work with the exception that the former grants an additional security layer by means of data encryption. Such proxies are useful in cases where secure communication is required, such as online banking, secure API communication, and data transfers. While HTTPS Proxies will sometimes slow down Internet speeds because of the encryption in data, the protection against cybersecurity breaches is worth the sacrifice as the cost outweighs the benefits, so It can prevent and defend against Man-in-the-middle MitM attacks.
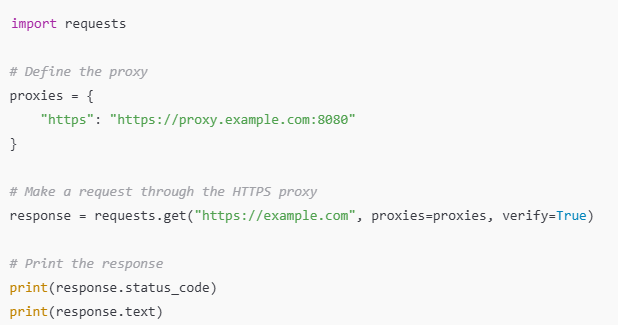
Example of an HTTPS Proxy Configuration
Here is an example of an HTTPS proxy in Python and the requests library and how one can configure it:
Explanation
- The proxy dictionary describes the HTTPS proxy address.
- requests.get sends a GET request to the secure URL using the proxy.
- The verify=True parameter ensures SSL/TLS certificates are verified.
- The response displays the status code and content of the secure webpage.
This example shows how an HTTPS proxy supplements regular web traffic encryption, which is vital in supporting data transfers over sensitive transactions.
Use Cases of HTTP and HTTPS Proxies
HTTP and HTTPS proxies find use in a variety of sectors and situations in order to better handle internet traffic and increase their security and privacy. Although their core function as intermediaries remains the same, their differentiating features make them applicable to different objectives. Below, we’ll mention the common and specific use cases for HTTP and HTTPS proxies.
1. Content Filtering and Access Control
- HTTP Proxy: It is common practice within organizations to employ an HTTP proxy, so their employees would not have access to certain websites or even a specific category of content. A good example would be that companies do not want employees to use social media while being at the office during the day, so they place such restrictions. Schools and educational institutions use HTTP proxies to restrict inappropriate content.
- HTTPS Proxy: Sometimes, it is a requirement for various tasks to inspect content on secure connections, and for this purpose, an HTTPS proxy is used. HTTPS proxies are able to decrypt and inspect encrypted traffic, which makes it especially important for secure sites that are trying to follow company policies.
- Example Use Case: For instance, an IT department in a large company utilizes the HTTPS proxy, which regulates encrypted traffic and prevents users from browsing prohibited IT Proxy servers.
2. Web Scraping and Data Extraction
- HTTP Proxy: For non-secure website scraping purposes, HTTP proxies are the most frequently used because of their speed and ease of support. Through these proxies, a user can send numerous requests without the need to expose their real IP address and avoid being detected or banned.
- HTTPS Proxy: These proxies scrape data from e-commerce, banks, API websites, and places secured by HTTPS connections. They assist the scraper in keeping the encryption level for sensitive data under control.
- Example Use Case: A market research analyst makes use of an HTTPS proxy to scrape encrypted e-commerce API data for price comparison.
3. Privacy and Anonymity
- HTTP Proxy: Web scrapers and scraping tools employ HTTP proxies to cloak their IP addresses; thus, they pose a challenge to some websites when attempting to follow users. However, encryption fails to secure sensitive operations due to its absence.
- HTTPS Proxy: HTTPS proxies are one level better than the former because they guarantee privacy because traffic is encrypted and not accessible to other people. They are helpful in the case of clandestine activities such as using public wifi networks for web browsing.
- Example Use Case: A journalist uses an HTTPS proxy for surveillance-free and tracking-free online research for sensitive issues.
4. Caching and Performance Optimization
- HTTP Proxy: HTTP proxies are widely deployed as a means of caching certain resources, such as images, videos, and CSS files. The load on the server is thereby reduced, resulting in a faster speed of sites’ loading, especially for frequently utilized resources.
- HTTPS Proxy: With HTTPS, caching is considerably more difficult due to the encryption that occurs, but some sophisticated HTTPS proxies are able to cache data from reputable, secure websites after they have decrypted the content.
- Example Use Case: Streaming services apply the use of HTTP proxies to cache frequently requested videos so that all users can view them globally with less latency.
5. Geo-Restriction Bypass
- HTTP Proxy: There are situations whereby people use HTTP proxies to bypass geo restrictions on certain websites/streaming services, and this is why they are often used. It becomes possible to access location-based material by having outbound traffic routed through an appropriate proxy.
- HTTPS Proxy: Instead, geo-blocking is circumvented with HTTPS proxies in an encrypted stream such that an individual’s traffic can not be seen by an ISP or other government actors.
- Example Use Case: An employee would like to use region-locked tools while traveling, and they can achieve this by using an HTTPS proxy.
6. Security and Threat Prevention
- HTTP Proxy: In the area of preventing cyber threats, such proxies might be considered to be unreliable since they are not encrypted. Nonetheless, they can still deny or filter out some domains or content in order to reduce the impact on the user.
- HTTPS Proxy: Focuses on threat mitigation by decoding and inspecting encrypted traffic before blocking malicious content, phishing websites, or activities of a suspicious nature.
- Example Use Case: An organization uses an HTTPS proxy in order to examine encrypted traffic and eliminate phishing attacks directed at employees.
7. API Communication
- HTTP Proxy: Anvil proxies facilitate and control API communication that is not secured. This is mostly very relevant for internal networks where encryption is not very necessary.
- HTTPS Proxy: Used especially in the context of financial services, healthcare, and e-commerce, wherein integrity and confidentiality of data are very important, HTTPS proxies assist with API communication in a secure manner.
- Example Use case: During the course of a financial transaction, a fintech company makes use of HTTPS proxies to deal with API requests.
HTTP vs HTTPS Proxy
HTTP and HTTPS proxies are both intermediary services that sit between clients and servers, but they are markedly different in their capabilities, security provisions and servers they can be used for.
HTTP servers and proxies do not consider data to be encrypted, so they do not cater to that need. This also means that the speeds are much higher as encryption is not a requirement, which means more cache for static content, web-scraping, and geo-restrictions are easier to bypass. But data passed through these servers remains unsecured and encrypted and is prone to being intercepted which means data breaches and eavesdropping are entirely possible.
HTTPS servers and proxies operate using SSL or TLS secure protocols to encrypt communication and act as intermediates, meaning anyone trying to snoop cannot view sensitive information, restricting their access to important details like API communications, financial transactions, and login credentials. The downside to using HTTPS servers is that they are always slightly slower than normal servers because of having to decrypt messages but they do guarantee security against man-in-the-middle attacks and many more due to their encryption and the use of these secure protocols.
For fast and quick transactions where security isn’t a concern, HTTP proxies work much better, whereas if a transaction is sensitive and requires multiple layers of security to be in place, HTTPS is the better option.
HTTP – Pros and Cons
HTTP proxies boast convenience, speed, and caching. However, they aren’t suited for handling sensitive data due to their lack of encryption. These proxies ensure efficiency while having major security compromises, thus making them a non-ideal solution for sensitive tasks.
Pros of HTTP Proxies
- Faster Performance: Traffic encryption is not employed, thus providing rapid reactivity and minimal delay.
- Efficient Caching: Resources on a server are saved due to web pages, videos, images, etc, being stored and recalled when required instead of creating them again.
- Efficient Caching: The difficulty associated with encryption makes installation and maintenance of the http-type proxies simple.
- Ideal for Non-Sensitive Tasks: Non-sensitive tasks such as content-based information filtering web scraping are perfect for this type of proxy.
- Cost-Effective: Less expensive to use and easier to maintain.
Cons of HTTP Proxies
- Lack of Encryption: Communication facilitated by HTTP proxies is not encased in encryption. Hence, the data is vulnerable to snooping and eavesdropping.
- Security Risks: These proxies are prone to numerous cyber attacks, MitM f.e.
- Not Suitable for Sensitive Data: Applications such as handling financial data, login information, or encrypted communication are not apt for these proxies.
- No Data Integrity Assurance: integrity will not be facilitated in data, which has a chance of getting altered at the time of its transmission.
Even though HTTP proxies are easy to use and clearly efficient, they are most definitely lacking when it comes to sensitive or private data.
HTTPS – Pros and Cons
Proxies for HTTPS maintain the integrity of the data during transfer by providing encryption, ensuring security and protection against malicious entities. However, these proxies are considerably slower, have a more complicated setup, and consume more resources than HTTP proxies. Recommended for sensitive operations.
Pros of HTTPS Proxies
- Enhanced Security: HTTPS proxies integrate SSL TLS encryption with the data they relay, hence preventing any interception or access for any unauthorized user.
- Data Integrity: Guarantees data to be transferred unchanged in order to assure its truthfulness.
- Protection Against Cyber Threats: Effective against Man in the Middle frauds and other cyber attacks.
- Secure API Communication: Necessary for the safe use of APIs in finance, healthcare, e-commerce, and other industries.
- Anonymity and Privacy: Encrypts what users do so that ISPs and other companies cannot see users’ actions online or track them.
Cons of HTTPS Proxies
- Slower Performance: The burden of encryption and decryption adds a delay to HTTPS proxies lowering their speed when compared to the HTTP proxies.
- Complex Configuration: To facilitate the use of HTTPS proxies, possessing technical knowledge of setting up and managing the SSL/TLS certificates is a requirement.
- Higher Resource Consumption: The use of encryption methods demands additional server resources, which leads to a high increase in operational costs.
- Caching Limitations: It is cumbersome to have to decrypt and then encrypt data merely to cache encrypted content, resulting in increased bandwidth usage.
HTTPS proxies perform remarkably well in terms of data security and protection. They sacrifice speed, complexity, and resource requirements.
Conclusion
HTTPS and HTTP proxies are essential for the maintenance of web traffic privacy and the optimization of the network. HTTP proxies are highly regarded for their speed, caching, and simplicity but cannot be used for sensitive data as these provide no form of encryption. HTTPS proxies, on the other hand, exceed in terms of security, data integrity, and protection against malicious intent and cyber attacks. However, these have slightly increased latency and require greater resources. Ultimately, the requirements between the two depend on the nature of the tasks. HTTP is preferred when security is not a concern, and HTTPS is used for secure communication and for protecting sensitive information.
FAQs
What’s the difference between HTTP and HTTPS proxies?
An HTTP proxy intercepts and forwards web (HTTP) traffic, allowing features like caching, filtering, and header manipulation - because it can read the content of requests. In contrast, an HTTPS proxy (using the CONNECT method) establishes an encrypted tunnel, passing traffic without inspecting it, making it more secure and private.
When should I choose HTTP vs. HTTPS proxy?
Use an HTTP proxy for fast, straightforward tasks like basic web browsing, caching content, or non-sensitive scraping. Opt for an HTTPS proxy when security matters - such as handling logins, sensitive data, or bypassing strict anti-bot defenses - thanks to its encryption.
Share this article:
Table of Contents
Proxies at $1
Get unlimited possibilities